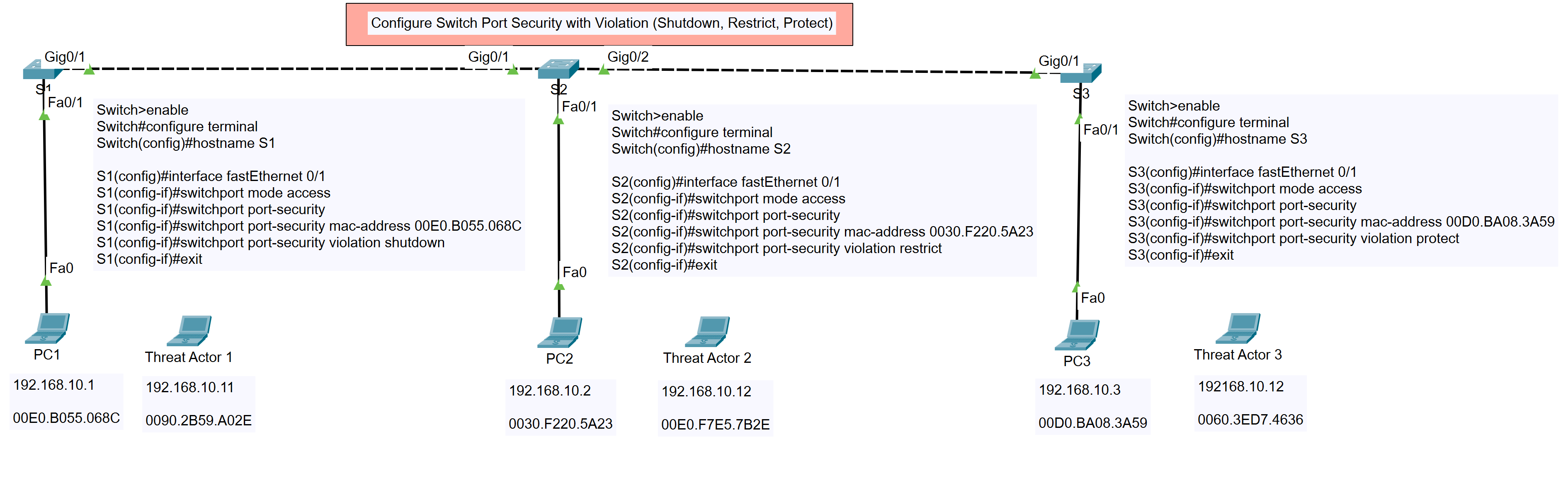
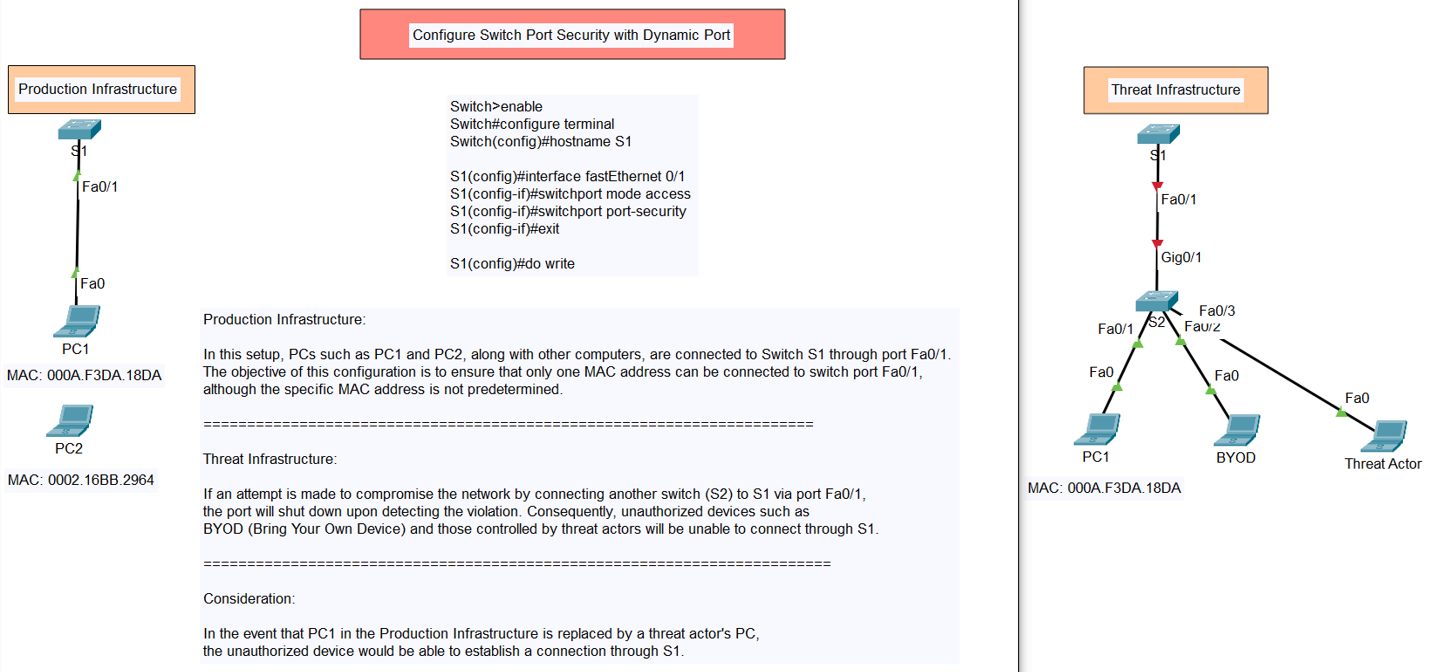
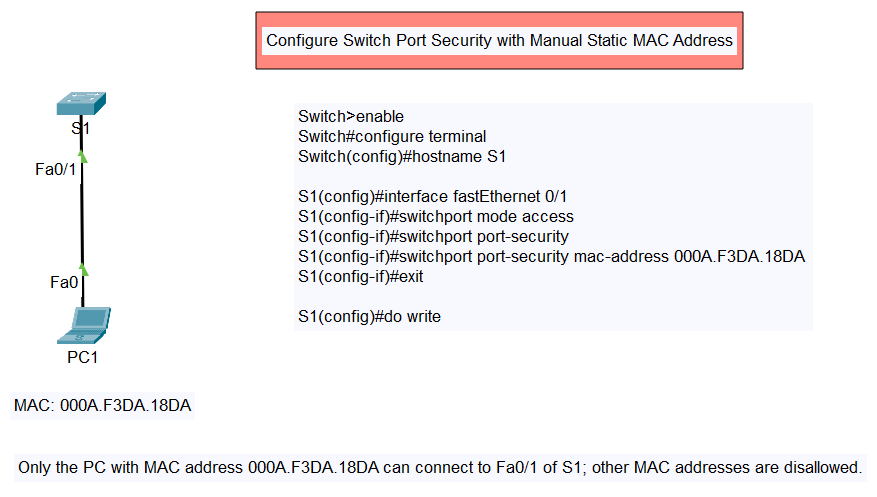
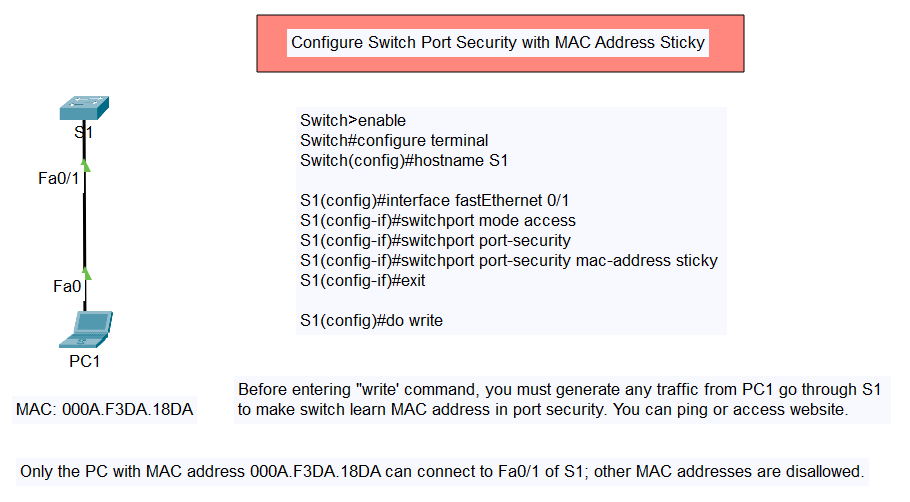
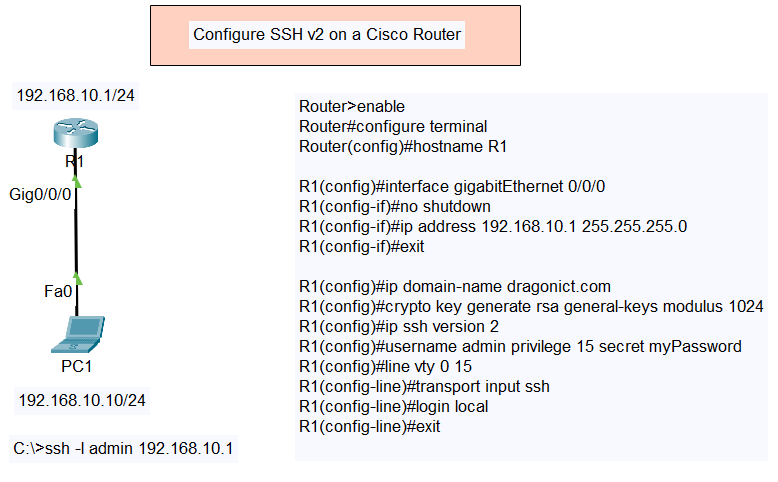
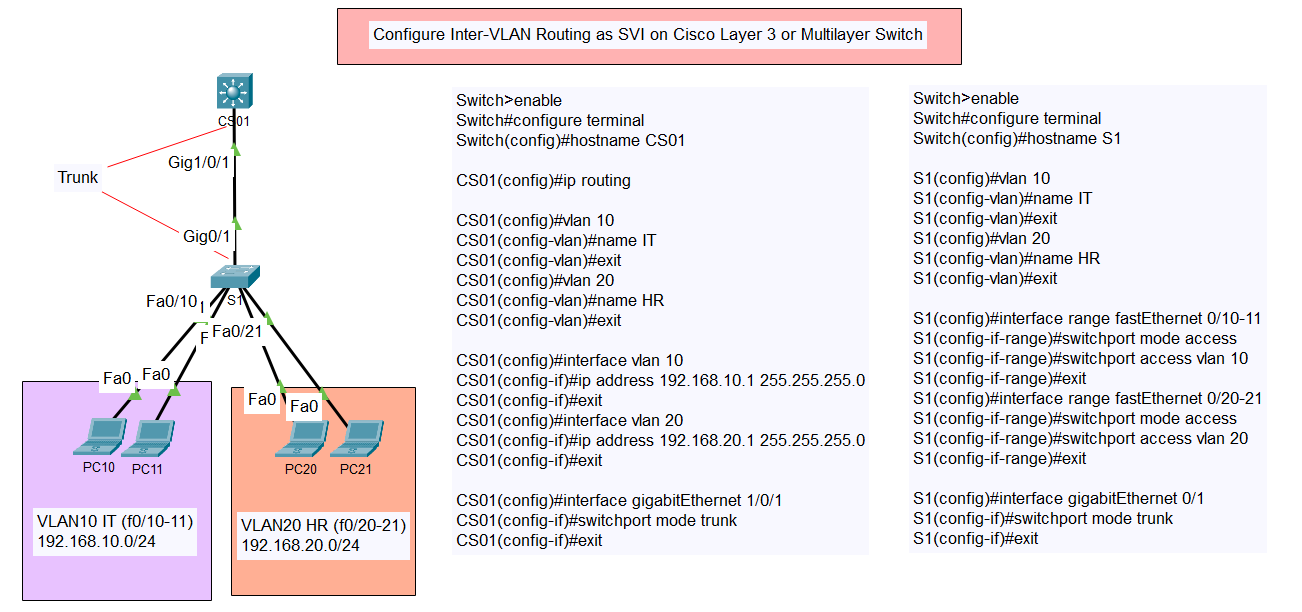
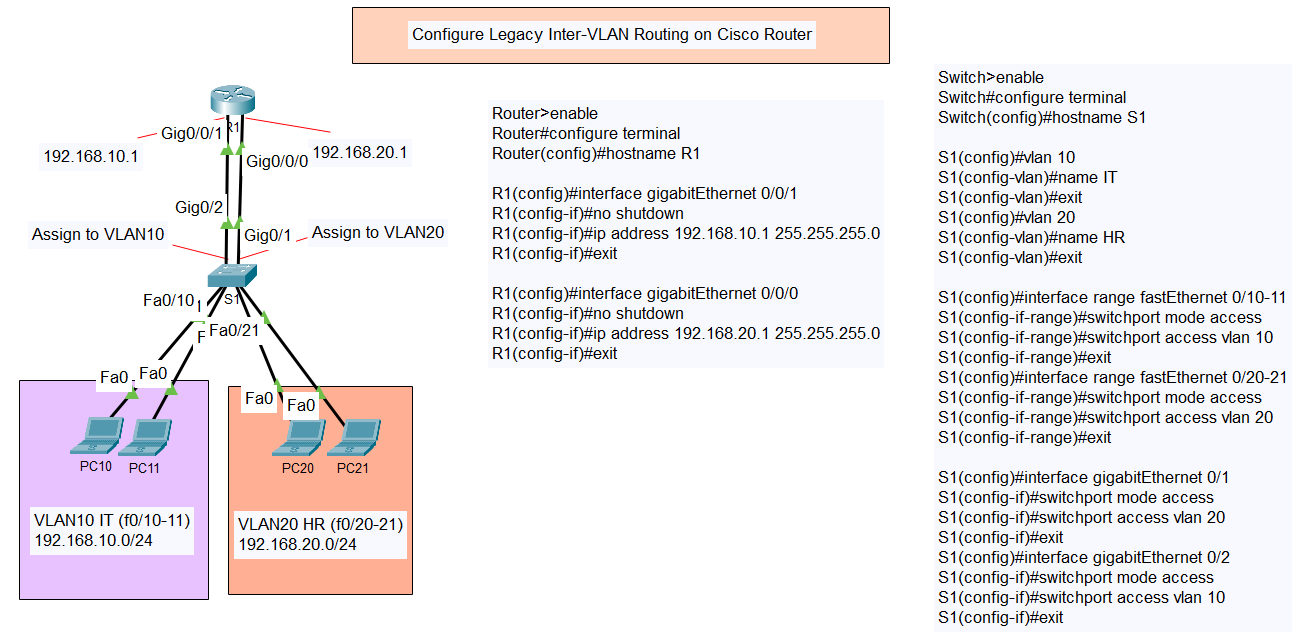
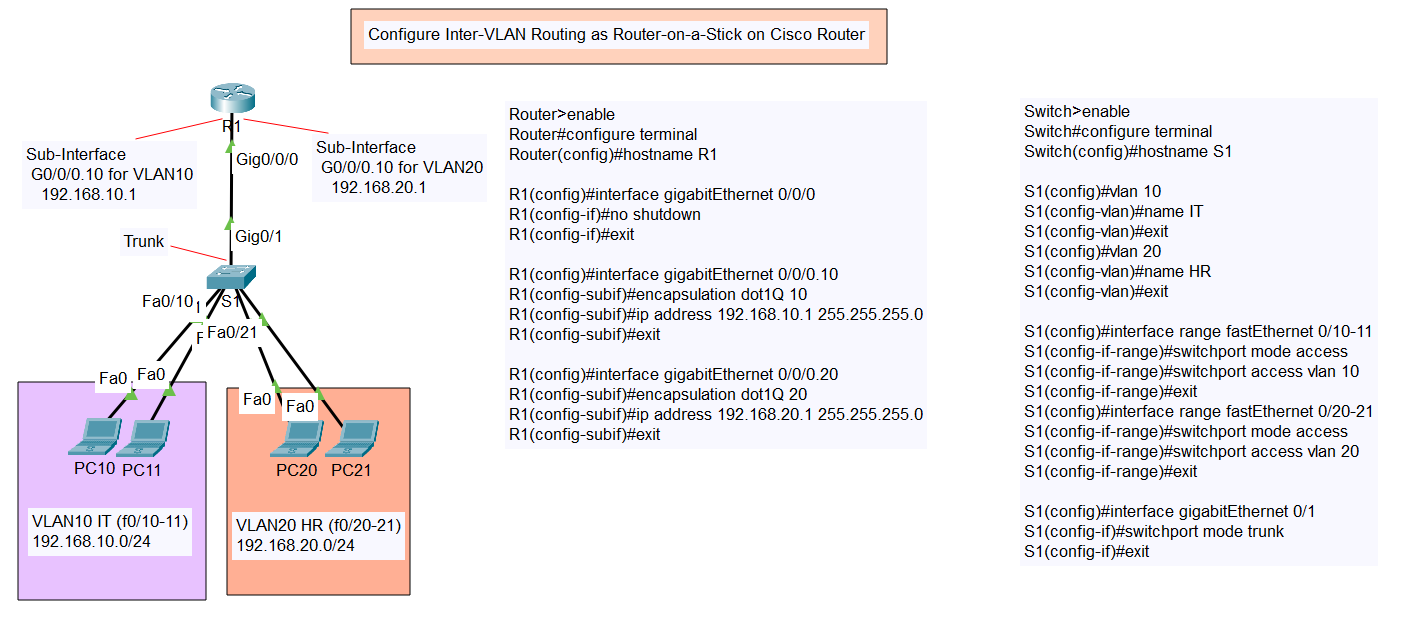
Configure Switch Port Security with Violation (Shutdown, Restrict, Protect)
Configure Switch Port Security with Violation (Shutdown, Restrict, Protect) In this tutorial, we will configure switch port security with three different violation modes: Shutdown, Restrict, and Protect. The topology used…