Configure Switch Port Security with Violation (Shutdown, Restrict, Protect)
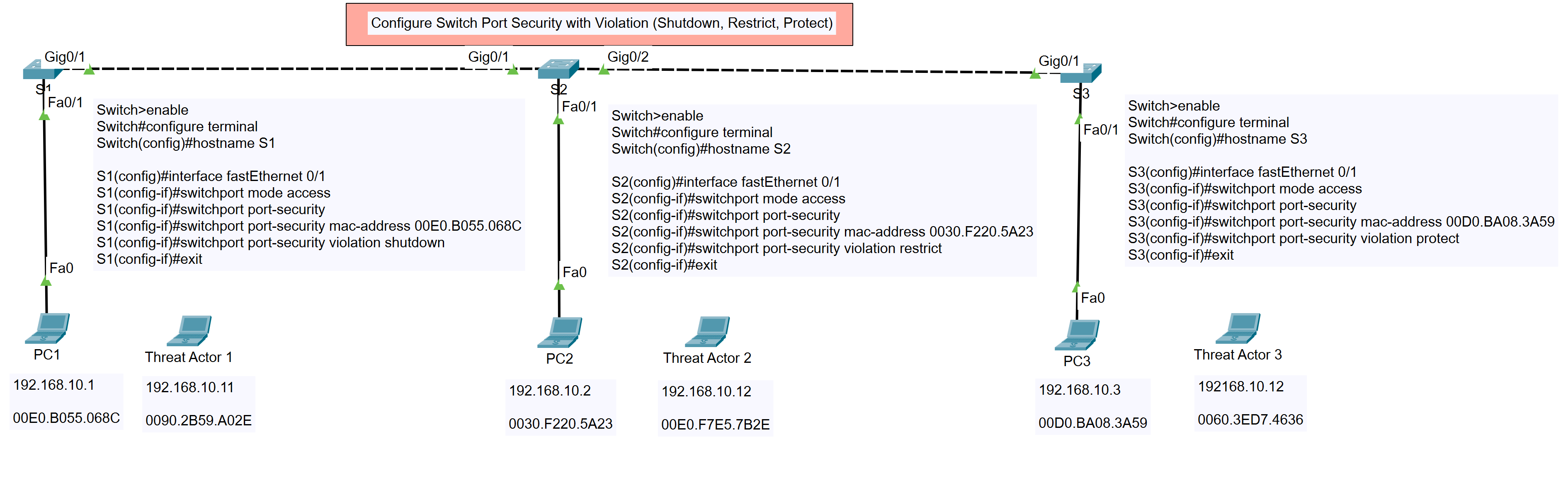
In this tutorial, we will configure switch port security with three different violation modes: Shutdown, Restrict, and Protect. The topology used is shown below:
Topology
Type of Switch Port Security
- Switch Port Security with Dynamic Port
- Switch Port Security with Manual Static MAC Address
- Switch Port Security with MAC Address Sticky
- Switch Port Security with Violation (Shutdown, Restrict, Protect)
Step 1: Configuring Port Security on Switch S1 (Shutdown)
Enter Global Configuration Mode
Switch>enable Switch#configure terminal Switch(config)#hostname S1
Configure Interface FastEthernet 0/1
S1(config)#interface fastEthernet 0/1 S1(config-if)#switchport mode access S1(config-if)#switchport port-security S1(config-if)#switchport port-security mac-address 00E0.B055.068C S1(config-if)#switchport port-security violation shutdown S1(config-if)#exit
Step 2: Configuring Port Security on Switch S2 (Restrict)
Enter Global Configuration Mode
Switch>enable Switch#configure terminal Switch(config)#hostname S2
Configure Interface FastEthernet 0/1
S2(config)#interface fastEthernet 0/1 S2(config-if)#switchport mode access S2(config-if)#switchport port-security S2(config-if)#switchport port-security mac-address 0030.F220.5A23 S2(config-if)#switchport port-security violation restrict S2(config-if)#exit
Step 3: Configuring Port Security on Switch S3 (Protect)
Enter Global Configuration Mode
Switch>enable Switch#configure terminal Switch(config)#hostname S3
Configure Interface FastEthernet 0/1
S3(config)#interface fastEthernet 0/1 S3(config-if)#switchport mode access S3(config-if)#switchport port-security S3(config-if)#switchport port-security mac-address 00D0.BA08.3A59 S3(config-if)#switchport port-security violation protect S3(config-if)#exit
Verification and Analysis of Violation Modes
Protect Mode
Status After Violation:
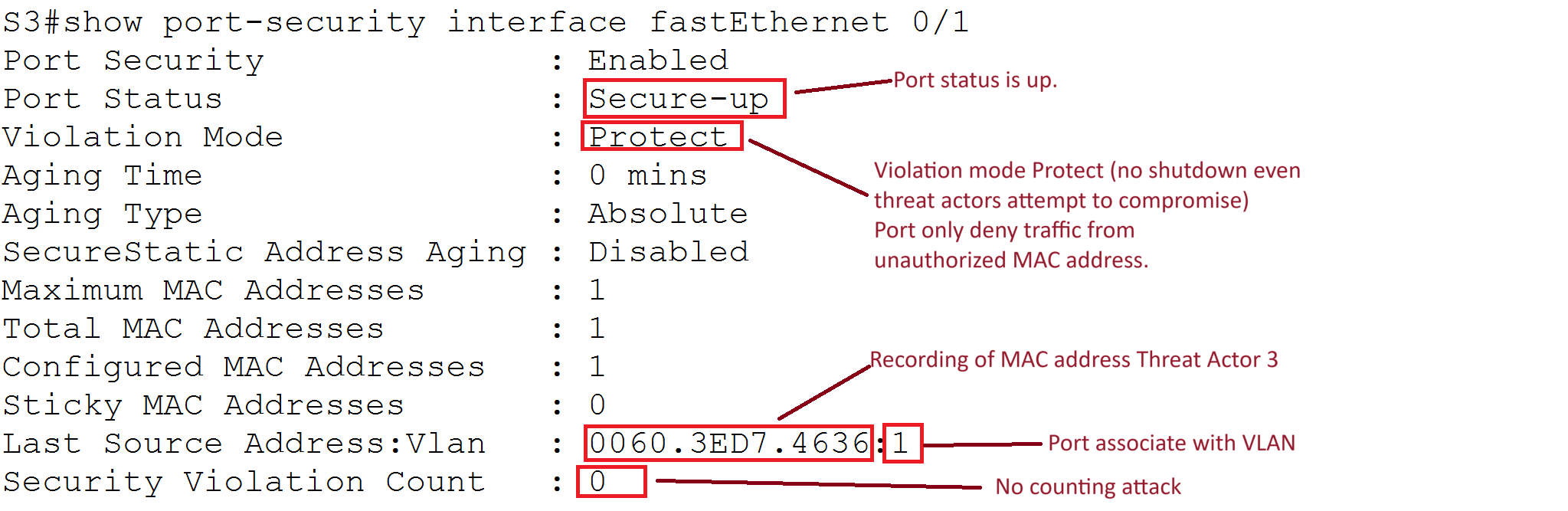
Explanation:
- Port Status: Secure-up
- Violation Mode: Protect
- Description: The port remains up and only denies traffic from unauthorized MAC addresses. No violation count is recorded.
Restrict Mode
Status After Violation:
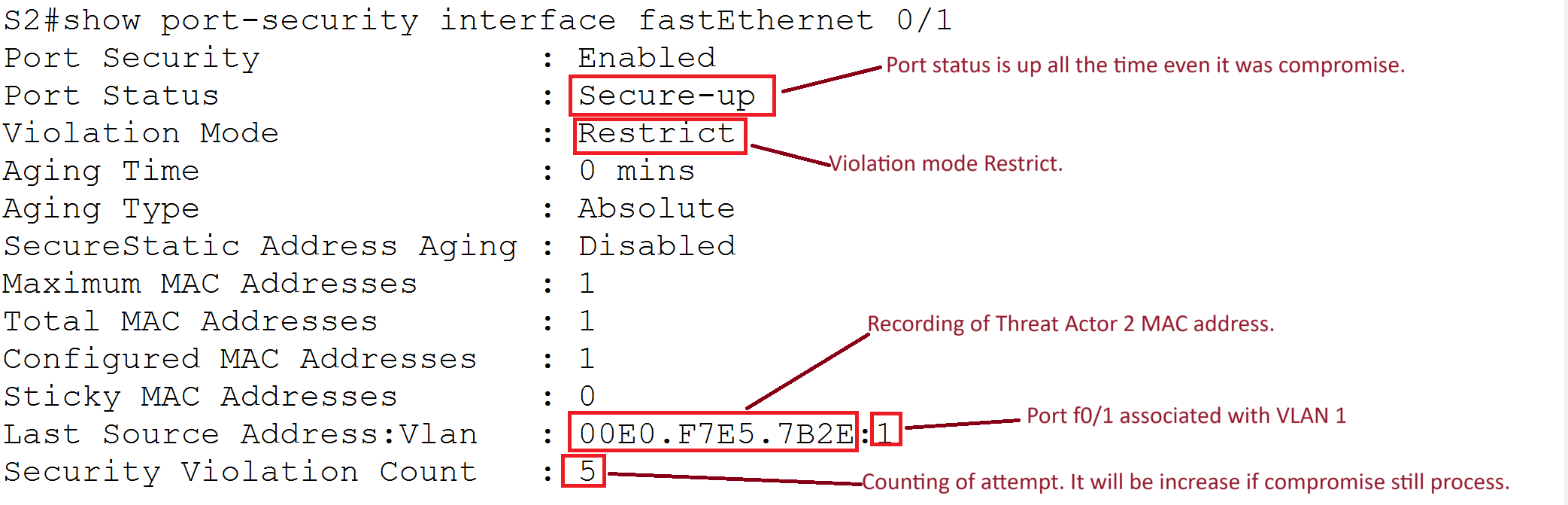
Explanation:
- Port Status: Secure-up
- Violation Mode: Restrict
- Description: The port remains up and denies traffic from unauthorized MAC addresses. The violation count increases with each attempt.
Shutdown Mode
Status After Violation:
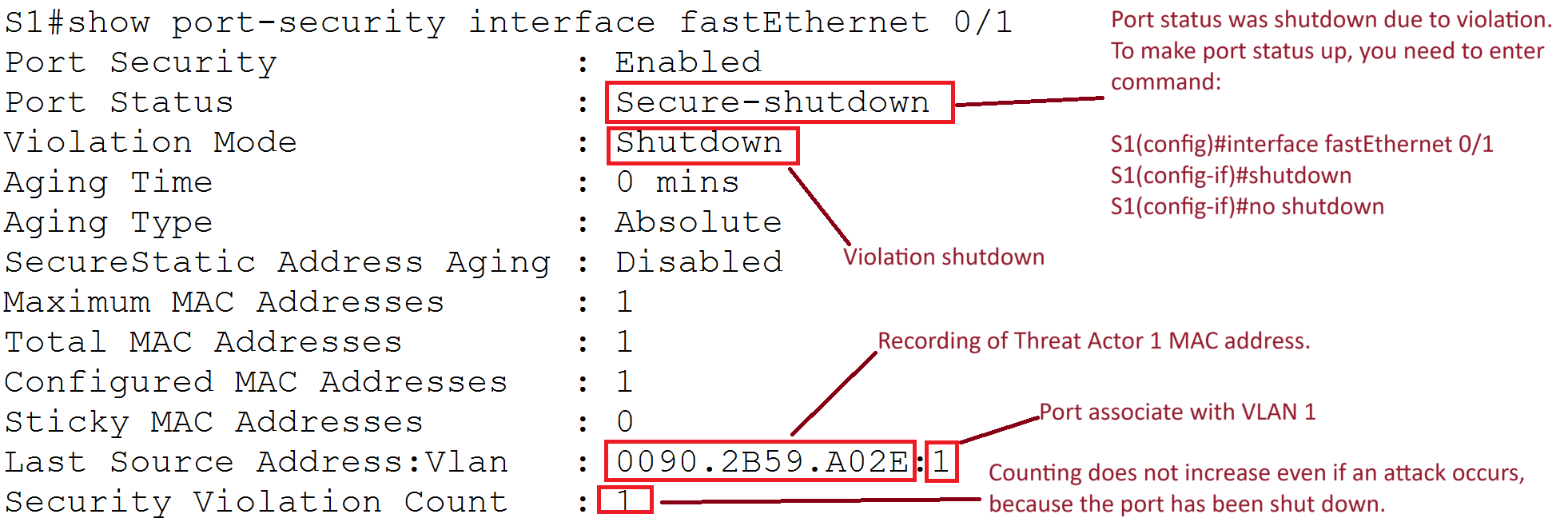
Explanation:
- Port Status: Secure-shutdown
- Violation Mode: Shutdown
- Description: The port shuts down upon violation. Counting does not increase after the port is shut down.
Conclusion
Port security is crucial for protecting network access. Each violation mode offers different levels of security based on the needs of your network. The Protect mode prevents unauthorized access without bringing the port down. The Restrict mode logs unauthorized access attempts while keeping the port up. The Shutdown mode provides the highest level of security by shutting down the port upon detecting a violation.
By implementing port security, you can ensure that only authorized devices are allowed on your network, reducing the risk of unauthorized access and potential security breaches.